A massive high severity vulnerability, with a CVSS (Common vulnerability scoring system) Score of 8.8, was found in a WordPress plugin called Download Manager.
The vulnerability made it possible for authenticated attackers to delete arbitrary files that are hosted on the server side.
This authenticated attacker would just need access in order to create downloads.
If this attacker were to delete the wp-config.php file, it would be possible to obtain administrative control.
This would also provide them with the ability to execute code. All they need to do is re-run the install process.
Wordfence recommends making sure that your site has been updated to the latest patched version of “Download Manager”. This version is reported as being 3.2.53.
What Are The Details of This Vulnerability?
The stats of Wordfence’s assessment are as follows:
Affected Plugin: Download Manager
Plugin Slug: download-manager
Plugin Developer: W3 Eden, Inc.
Affected Versions: <= 3.2.50 CVE ID: CVE-2022-2431 CVSS Score: 8.8 (High) CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H Researcher/s: Chloe Chamberland Fully Patched Version: 3.2.51
How Does This Vulnerability Work?
The major benefit of Download Manager is that it’s a WordPress plugin that’s been programmed to allow content creators to share downloadable files that are stored as posts.
And these downloads are displayed on the front-end of the site for users to download.
The vulnerable versions of the plugin have a bypass. This bypass affects how the downloadable file is saved on the server and then deleted on post deletion. This makes it easier for attackers to delete arbitrary files from the server.
Wordfence explains the following:
When looking at this function at first, it looks pretty safe. Especially if the file path is validated.
Unfortunately, with this vulnerability, this is not the case. The path to a file saved with “download” post is actually not validated in this case. Without this validation, it’s impossible to ensure it’s a safe file type or stored in a location that’s associated with a “download” post.
This means that any extension can be applied to a path to an arbitrary file using the file[files][ ] parameter as one would save a post.
This also means that this is the file that would physically be associated with that download post.
In many configurations of WordPress, any attacker could easily add a path, such as /var/www/html/wp-config.php, which associates a site’s WordPress configuration file with that download post.
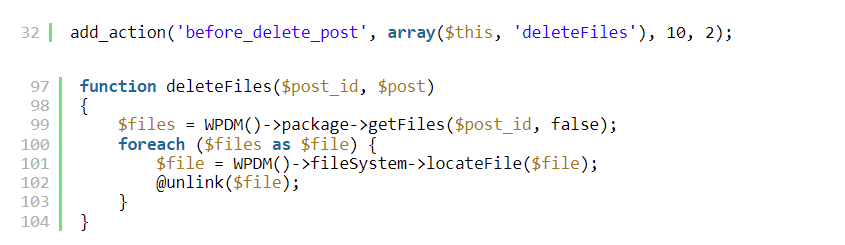
This is an example of the code that Wordfence shared:
So, what happens when the user navigates to actually delete the “download” post? This deleteFiles() code will be triggered by a hook called before_delete_post.
The supplied filename will physically be deleted, if it actually exists on the server.
Attackers can use this hack to delete critical files that are hosted on the server. In the case of the deletion of some of these files, this could potentially lead to a full site takeover by said bad actors.
Of particular interest to hackers is the wp-config.php file, because the deletion of this file results in disconnecting the current database from the site that’s been compromised.
This then allows the attacker to re-complete the install process, and enables them to actually connect their own database to the site.
With the connection of their own database, they would then have full access to the server. Consequently, they can upload more arbitrary files that could then result in further infection of the system.
This Vulnerability Requires Contributor Access and Over
Wordfence’s assessment also includes the fact that this vulnerability needs contributor access (or over) in order to exploit it.
This is a good reminder to always ensure that you don’t provide any significant access to any user who is untrusted.
You should also always validate that all of your users have strong, encrypted passwords to make sure that your site won’t fall victim to this kind of attack.
Or that your site doesn’t fall victim to unauthorized bad actors who may gain access through a compromised password.