Wordfence has reported that a severely critical increase in attempted attacks on a WPBakery vulnerability has been observed.
This particular vulnerability is known as an “arbitrary file upload” vulnerability, tracked as CVE-2021-24284, which was previously disclosed on April 21, 2021.
While the plugin has been closed, it hasn’t been patched.
Malicious PHP File Upload Capability
The nature of the vulnerability gives malicious attackers the ability to upload malicious PHP files to a website that has been impacted, which can lead to the taking over of an entire site.
Once a foothold has been established, malicious JavaScript can then be injected into files on the site, including certain other malicious activities that can be committed by the attackers.
Wordfence reports that all customers have been protected from this campaign since May 21, 2021 with Wordfence Premium implementing a brand-new firewall rule that helps mitigate these attacks.
It is strongly recommended by WordFence that you completely remove Kaswara Modern WPBakery Page Builder addons as soon as possible and work with an alternative.
They explain that it’s very unlikely that this addon is going to ever receive a patch.
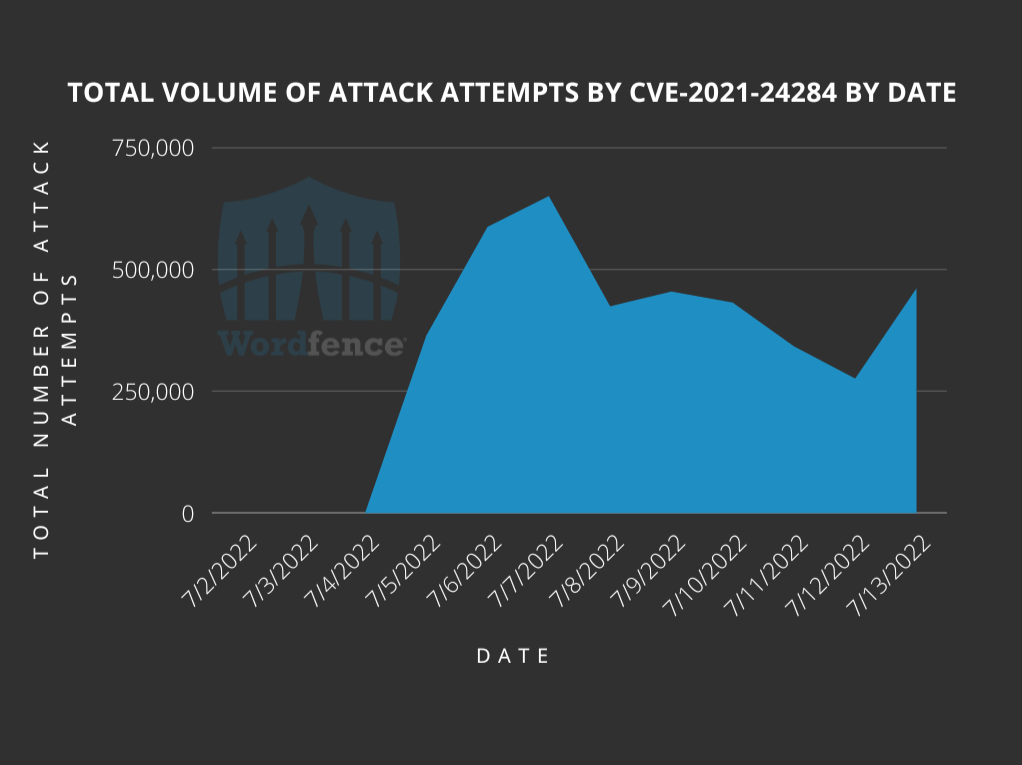
They report that they have blocked an average of 443,868 attack attempts per day that have been trying to attack the network of sites they have protected during the campaign.
Even though 1,599,852 unique websites were targeted, it’s important to note that a majority of these sites were not using the plugin that’s responsible for this vulnerability.
Source: https://www.wordfence.com/blog/2022/07/attacks-on-modern-wpbakery-page-builder-addons-vulnerability/
Statistics of The WPBakery Vulnerability
The following includes the statistics of the WPBakery vulnerability, which is comprised of a CVSS score of 10.0 (which is the highest score a vulnerability can get).
This makes this vulnerability an extremely high priority to resolve, if you are using this plugin.
- “Description: Arbitrary File Upload/Deletion and Other
- Affected Plugin: Kaswara Modern WPBakery Page Builder Addons
- Plugin Slug: kaswara
- Affected Versions: <= 3.0.1
- CVE ID:CVE-2021-24284
- CVSS Score: 10.0 (Critical)
- CVSS Vector:CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
- Fully Patched Version: NO AVAILABLE PATCH.”
What Are The Common Indications of an Attack?
Wordfence also reported that the majority of attacks they are observing send what’s called a POST request to the following file: /wp-admin/admin-ajax.php.
Attackers do this by using the uploadFontIcon AJAX action that’s part of this plugin.
Then, these attackers use the vulnerability to upload a file to the impacted website.
It’s possible that your logs could show a query string on the following event:
/wp-admin/admin-ajax.php?action=uploadFontIcon HTTP/1.1
The following IPs are apparently responsible for the majority of attacks, based on Wordfence’s report:
- “217.160.48.108 with 1,591,765 exploit attempts blocked
- 5.9.9.29 with 898,248 exploit attempts blocked
- 2.58.149.35 with 390,815 exploit attempts blocked
- 20.94.76.10 with 276,006 exploit attempts blocked
- 20.206.76.37 with 212,766 exploit attempts blocked
- 20.219.35.125 with 187,470 exploit attempts blocked
- 20.223.152.221 with 102,658 exploit attempts blocked
- 5.39.15.163 with 62,376 exploit attempts blocked
- 194.87.84.195 with 32,890 exploit attempts blocked
- 194.87.84.193 with 31,329 exploit attempts blocked”
What Are The Common Indicators That a Site was Compromised?
Currently, there are limited indications that webmasters can use to determine whether their site has been compromised by this attack.
But, Wordfence recommends, based on the vulnerability’s functionality, checking /wp-content/uploads/kaswara/ directory along with any and all subdirectories for PHP files associated with this directory.
However, they have found the following common files on sites that have been affected by this hacker attack:
- /wp-content/uploads/kaswara/icons/kntl/img.php
- /wp-content/uploads/kaswara/fonts_icon/15/icons.php
- /wp-content/uploads/kaswara/icons/brt/t.php
- /wp-content/uploads/kaswara/fonts_icon/jg4/coder.php
Ultimately, This is An Actively-Exploited Zero-day Vulnerability
The major issue affecting this particular plugin is the fact that this plugin has many flaws that have significant vulnerabilities that attackers who are unauthenticated by the server can take advantage of to perform malicious acts.
Attackers can upload malicious files, and these files can be used to take over ownership of a website entirely.
Because the plugin is unpatched, the recommendation is to deactivate and remove the plugin immediately.
After doing this, you will need to find an alternative that has not been affected by any malicious attacks.