A vulnerability has been reported by Wordfence in the WordPress plugin OptinMonster.
This vulnerability results in any unauthenticated attacker being given the ability to export sensitive content, and they can also inject malicious JavaScript code to WordPress sites.
These are just two of the actions they can take, though there are other possibilities.
We strongly recommend that anyone using OptinMonster update their plugins immediately.
How Severe is This Vulnerability?
Wordfence rates the severity of this vulnerability with a CVSS score of 7.2, which is on the high end of the spectrum.
The CVSS acronym is known as the Common Vulnerability Scoring System.
This is a way to communicate how severe a specific vulnerability actually is, and produce a numerical score that’s easy for companies to use to prioritize their processes in order to tackle this vulnerability.
What is OptinMonster?
This plugin helps SEO professionals create sales campaigns by using dialogs in WordPress.
Both the plugin and the app website rely on API endpoints for seamless integration.
By using API endpoints, the design process is also seamlessly integrated.
The unfortunate issue is that the REST-API endpoints were not implemented securely. This makes it possible for attackers to access them even though they are unauthenticated.
Allowing unauthenticated users is not only a huge security issue, but it also leaves vulnerable sites open to complete takeovers by malicious attackers.
The /wp-json/omapp/v1/support endpoint is what is most critical. This endpoint disclosed data that’s normally considered sensitive, including the site’s full path on the server.
The API key that was necessary to make server requests on OptinMonster’s website was also shown, which allowed attackers to see that and take advantage of it.
In normal secure implementations, the API key is hidden from prying eyes, and it takes a lot of effort just to uncover it.
In addition, the most severe issue is that attackers did not even need low-level authentication in order to access that API endpoint.
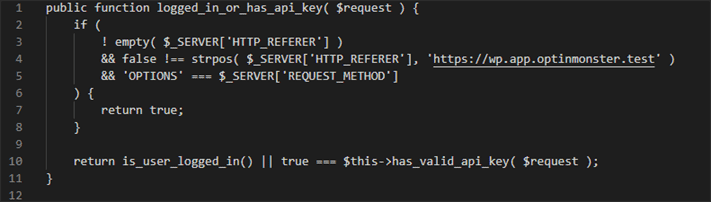
One of the functions – logged_in_or_has_api_key – used as the permissions_callback was insecurely implemented, which resulted in an endpoint not needing such authentication.
For example: if any request was sent to the API endpoint, and the Referer header was set to https://wp.app.optinmonster.test, and the HTTP type of request was set to OPTIONS, then this function would actually return the value of ‘true’.
What does this mean, exactly? This insecurity means that that request would pass the capability check.
According to Wordfence:
So basically any attacker without authentication had the ability to add malicious JavaScript code to a site that was running OptinMonster, ultimately leading to visitors being sent to external bad domains, as well as sites being taken over by JavaScript injection, or they could overwrite the code of a plugin with webshell in order to gain access to a site’s backdoors.
We Recommend Updating Your Plugins
As usual, we recommend updating your plugins if you have been negatively impacted by this vulnerability.
Although, if you have been impacted, you would likely know it by now.
Either way, the updating of this plugin should help remove any instances of this vulnerability as a result.